Introduction: Why You Should Stay Updated on What's New in Cybersecurity
The digital landscape is evolving faster than ever, and with it comes a constant wave of cybersecurity threats and solutions. For businesses, IT professionals, and everyday users, staying updated with what’s new in cybersecurity isn’t optional—it’s essential.
Each month brings fresh challenges and developments. Whether it’s a new malware strain, the rise of ransomware-as-a-service, or groundbreaking solutions in network security insights, understanding these changes can be the difference between protection and vulnerability.
This monthly cybersecurity roundup offers a digestible and expert summary of the most impactful developments, supported with actionable insights to keep you and your organization ahead of the curve.
1. Cybersecurity Trends Dominating This Month
AI-Driven Threat Detection Becomes Mainstream
Artificial Intelligence is not just a buzzword anymore. In April, leading cybersecurity firms like CrowdStrike and Palo Alto Networks rolled out AI-powered updates for real-time threat detection. These AI models are becoming smarter at identifying anomalies and phishing tactics, thereby reducing response times significantly.
Expert Tip: Businesses should invest in AI-based threat intelligence tools to anticipate and neutralize threats proactively.
Quantum-Resistant Encryption Gaining Ground
The rise of quantum computing has prompted new standards in encryption. NIST’s post-quantum cryptography algorithm recommendations are now being adopted by tech giants, signaling a shift toward future-proofing data.
Internal Linking Opportunity: Link to an article like The Rise of Quantum Computing: What It Means for Businesses.
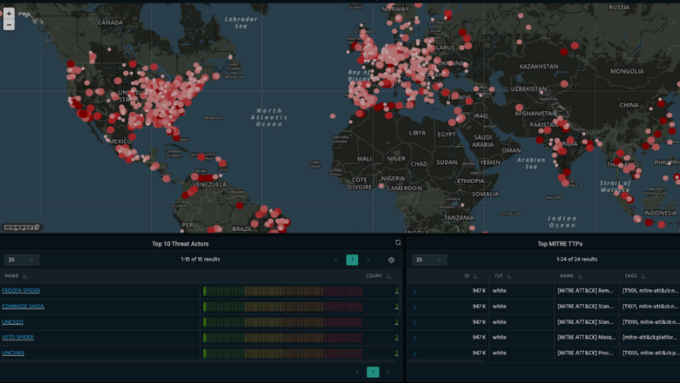
2. Major Data Breach Updates You Need to Know
This month has seen several high-profile breaches, reinforcing the need for better data governance and threat response.
TicketMaster & LendingTree Breaches
TicketMaster: Exposed personal data of over 250,000 users due to third-party script vulnerabilities.
LendingTree: A credential stuffing attack led to unauthorized access to thousands of customer records.
These incidents underline how even large corporations are not immune. The growing sophistication of cybercriminals calls for businesses to review their access controls and multi-factor authentication protocols.
Takeaway: Regular audits and penetration testing can help mitigate the risk of such breaches.
SMBs Increasingly Targeted
New data from IBM shows that 43% of cyberattacks in Q2 2025 were aimed at small and medium-sized businesses. The misconception that smaller companies are “safe” from attacks is no longer valid.

3. Threat Intelligence Reports Highlight Rising Nation-State Attacks
Nation-state cyberattacks are surging, particularly those originating from North Korea, Russia, and Iran. In this month’s threat intelligence reports from Mandiant and Microsoft, it’s clear that geopolitics is now deeply intertwined with cyber warfare.
The Rise of Wiper Malware
Unlike ransomware, which seeks financial gain, wiper malware aims to destroy data, making recovery impossible. This type of malware has been observed in recent conflicts and is often deployed as part of hybrid warfare tactics.
Security Suggestion: Invest in air-gapped backups and secure DNS-layer protection.
Threat Intelligence Tools Evolving
Platforms like Recorded Future and ThreatConnect are now integrating predictive analytics to help companies anticipate attacks before they occur.
Internal Linking Opportunity: Link to guides on “Best Threat Intelligence Tools in 2025” or “How to Set Up a Cybersecurity Defense Plan”.

3. Threat Intelligence Reports Highlight Rising Nation-State Attacks
Nation-state cyberattacks are surging, particularly those originating from North Korea, Russia, and Iran. In this month’s threat intelligence reports from Mandiant and Microsoft, it’s clear that geopolitics is now deeply intertwined with cyber warfare.
The Rise of Wiper Malware
Unlike ransomware, which seeks financial gain, wiper malware aims to destroy data, making recovery impossible. This type of malware has been observed in recent conflicts and is often deployed as part of hybrid warfare tactics.
Security Suggestion: Invest in air-gapped backups and secure DNS-layer protection.
Threat Intelligence Tools Evolving
Platforms like Recorded Future and ThreatConnect are now integrating predictive analytics to help companies anticipate attacks before they occur.
Internal Linking Opportunity: Link to guides on “Best Threat Intelligence Tools in 2025” or “How to Set Up a Cybersecurity Defense Plan”.

4. Ransomware News: New Variants and Tactics
Ransomware continues to evolve with more aggressive tactics, including data exfiltration and triple extortion (targeting victims, customers, and partners).
LockBit 4.0 Makes a Comeback
After being briefly disrupted by law enforcement, the LockBit gang has returned with a more resilient and stealthier version—LockBit 4.0. It uses sandbox evasion techniques, making it harder for antivirus programs to detect.
Advice for IT Teams: Regularly update endpoint detection and response (EDR) solutions and train employees on phishing prevention.
Ransomware-as-a-Service (RaaS) on the Rise
The “democratization” of ransomware via subscription models has lowered the barrier for entry for cybercriminals. New RaaS groups like “Silent Spider” are offering customizable malware kits for as little as $300/month.
Pro Insight: Monitor dark web forums for signs of your brand’s compromise using cyber threat intelligence services.
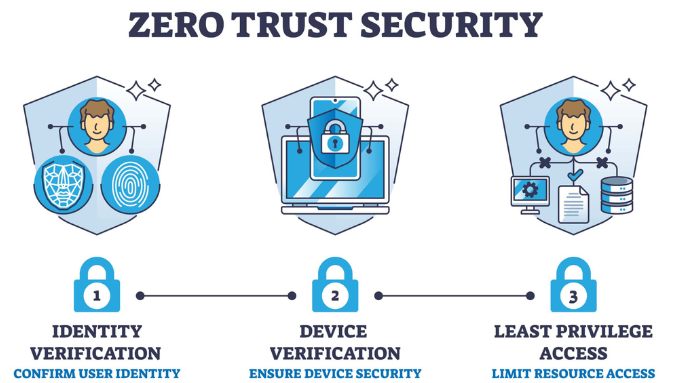
5. Network Security Insights: Modernizing Infrastructure
o combat advanced persistent threats (APTs), businesses are shifting to zero-trust architecture and SASE (Secure Access Service Edge) frameworks.
Zero Trust is the New Normal
Google’s BeyondCorp model has now become an industry standard. Instead of trusting users by default, zero-trust mandates verification at every access point.
Cloud Security Challenges
More enterprises are moving to multi-cloud environments, but many overlook security configurations. Misconfigured AWS S3 buckets and exposed Azure containers continue to be a major issue.
Best Practice: Employ continuous monitoring tools that offer real-time network security insights and automate compliance checks.
Conclusion: How to Stay Ahead in a Changing Cybersecurity Landscape
Each month brings new challenges, threats, and innovations. Understanding what’s new in cybersecurity isn’t just about awareness—it’s about preparation.
With AI-driven tools, evolving attack tactics, and the increasing stakes of data protection, organizations need to be more proactive than ever. By leveraging the latest cybersecurity trends, maintaining up-to-date threat intelligence, and strengthening your network security, you’re not just reacting—you’re leading.
Stay informed. Stay secure.
