Introduction: The Evolving Cybersecurity Landscape in 2025
As digital transformation accelerates across all industries, cybersecurity threats in 2025 are becoming more sophisticated, targeted, and harder to detect. From ransomware variants enhanced by artificial intelligence to the growing complexity of cloud infrastructure vulnerabilities, businesses face a turbulent security future.
In this article, we explore the top 10 cybersecurity threats in 2025, how they affect organizations, and what proactive measures you should take to stay ahead.
1. AI-Driven Cyber Attacks: The Rise of Autonomous Hacking
AI-driven cyber attacks have emerged as one of the most dangerous developments in cybersecurity. Cybercriminals are now leveraging machine learning algorithms to:
Analyze security defenses
Create adaptive malware
Launch large-scale phishing campaigns
Exploit vulnerabilities faster than humans can respond
According to recent threat intelligence reports, AI-based attacks are capable of learning from failed attempts and refining their tactics in real-time, making them harder to detect.
🔗 Trending Term: Link to “What is AI in Cybersecurity?” for internal linking and SEO juice.
Expert Tip: Adopt AI-powered threat detection systems and conduct continuous behavioral analysis to neutralize such attacks.

2. Ransomware Evolution: From Files to Full Systems
Ransomware evolution has gone far beyond encrypting files. In 2025, attackers are increasingly:
Targeting IoT and operational technologies (OT)
Launching double-extortion attacks (data theft + encryption)
Demanding cryptocurrency payments through automated bots
New variants such as RaaS (Ransomware-as-a-Service) make it easy for non-technical criminals to deploy ransomware through subscription models.
🔗 Trending Term: Link to “How Ransomware-as-a-Service Is Disrupting Cybersecurity”
Expert Tip: Conduct frequent backups, store them offline, and test recovery plans to reduce downtime.

3. Cloud Security Risks: The Dark Side of Flexibility
The shift to hybrid and multi-cloud environments has introduced a wave of cloud security risks. Misconfigurations, weak identity management, and unsecured APIs are the most common entry points for cybercriminals in 2025.
Cloud breaches are especially damaging due to:
Scalability of attacks
Loss of customer trust
Difficulty tracing breach origins
🔗 Trending Term: Link to “Common Cloud Misconfiguration Mistakes”
Expert Tip: Enforce least-privilege access, use CSPM tools (Cloud Security Posture Management), and conduct frequent audits.
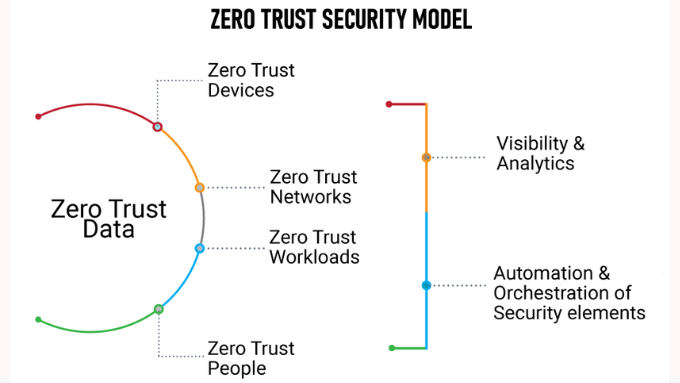
4. Zero Trust Architecture Under Attack
Zero Trust architecture was once hailed as a cybersecurity silver bullet. However, in 2025, attackers are now specifically targeting weaknesses in poorly implemented Zero Trust models.
They exploit:
Unpatched internal systems
Overly permissive microsegmentation
Inadequate identity verification methods
This is particularly risky for remote-first businesses and those scaling rapidly.
🔗 Trending Term: Link to “How to Implement Zero Trust Architecture the Right Way”
Expert Tip: Zero Trust is not a one-time setup. Continuously monitor user behavior, validate identities, and adapt your policies dynamically.
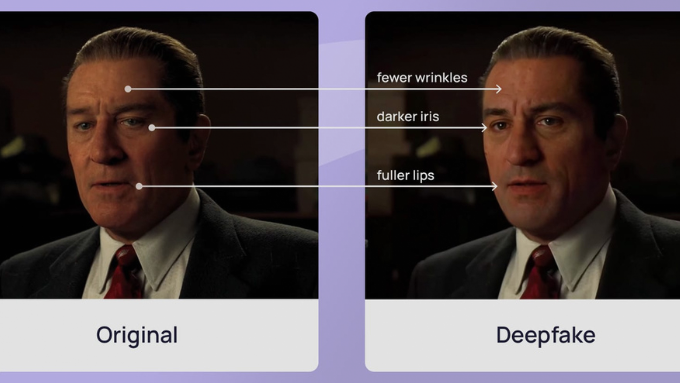
5. Deepfake and Social Engineering Attacks
In 2025, deepfake technology is enabling highly realistic impersonations of executives, allowing attackers to bypass traditional verification processes. Combined with advanced social engineering techniques, these attacks can:
Manipulate employees into approving fake transactions
Leak sensitive data unknowingly
Breach even secure communication channels
🔗 Trending Term: Link to “Recognizing Deepfake-Based Scams in Business Emails”
Expert Tip: Educate staff regularly, implement multi-factor authentication (MFA), and verify critical requests through multiple channels.
6. Exploitation of Remote and Hybrid Work Models
The continued trend of remote work has expanded the attack surface. Many home networks remain unprotected, and personal devices lack enterprise-grade security protocols. Threats include:
Unauthorized device access
Poorly secured Wi-Fi networks
Shadow IT practices
Expert Tip: Use enterprise VPNs, endpoint detection and response (EDR), and mobile device management (MDM) tools to protect remote endpoints.
🔗 Internal Link Suggestion: “Best Practices for Securing Remote Workforce in 2025”

7. Attacks on Critical Infrastructure and Smart Cities
As governments and corporations build out smart cities and digitize infrastructure, the risk of cyber attacks grows exponentially. Cybercriminals now target:
Transportation systems
Power grids
Water treatment facilities
Healthcare networks
These aren’t just data breaches — they could result in real-world harm.
Expert Tip: Critical infrastructure must be segmented from the internet, monitored in real-time, and include fail-safe protocols.
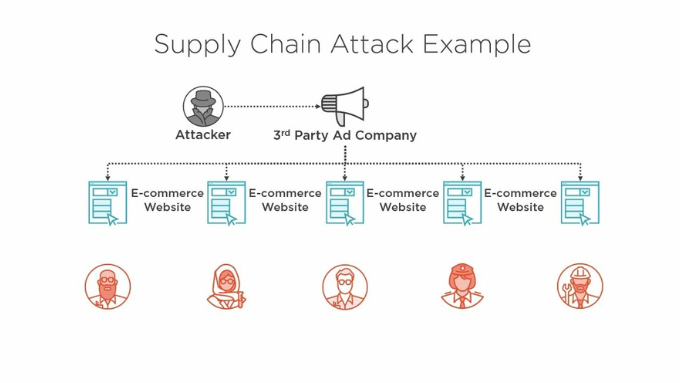
8. Supply Chain Attacks: The Hidden Cyber Bomb
Supply chain attacks are on the rise in 2025, with hackers infiltrating a trusted vendor or third-party tool to compromise multiple targets at once.
Recent examples show that even minor code updates from a trusted vendor can serve as a vector for large-scale intrusions. Attackers exploit the “trust” factor businesses place in their partners.
🔗 Trending Term: Link to “How to Prevent Software Supply Chain Attacks”
Expert Tip: Vet all third-party vendors, mandate code reviews, and use software bill of materials (SBOM) strategies.
9. Regulatory and Data Privacy Concerns
With stricter regulations like the AI Accountability Act and Global Data Protection Framework (GDPF), businesses must not only secure their systems but also ensure full compliance. Non-compliance results in:
Hefty fines
Brand damage
Legal consequences
Data breaches in 2025 can expose not just emails or passwords, but full biometric profiles and behavioral data.
Expert Tip: Implement a privacy-first data strategy and use compliance automation tools to stay ahead.
🔗 Internal Link Suggestion: “What You Need to Know About GDPR, CCPA, and GDPF in 2025”
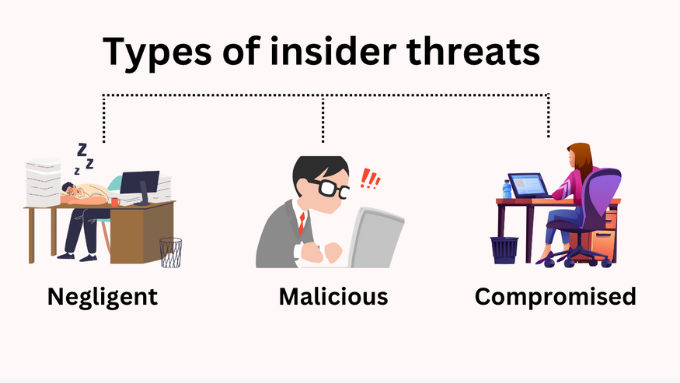
10. Insider Threats Enhanced by AI
Insider threats are no longer just about disgruntled employees. In 2025, attackers are recruiting insiders or manipulating them with AI-generated communications and incentives.
Risks include:
Credential sharing
Privilege misuse
Accidental data leaks
Expert Tip: Use user behavior analytics (UBA) and real-time access controls to monitor unusual internal activity.
🔗 Internal Link Suggestion: “How to Identify and Respond to Insider Threats”
Final Thoughts: Building a Resilient Cybersecurity Posture in 2025
The cybersecurity threats in 2025 aren’t just more sophisticated — they’re more personal, persistent, and pervasive. Businesses must think beyond firewalls and antivirus and focus on:
Threat intelligence
Employee training
Advanced analytics
Secure architecture design
Proactivity is no longer optional — it’s survival.
