Table of Contents
The Escalating Ransomware Landscape in 2025
Why Small- and Mid-Sized Businesses Are Prime Targets
Ransomware Protection Strategies: A 360° Blueprint
Building a Zero-Trust Security Framework
The Role of Endpoint Detection and Response (EDR)
Leveraging AI-Driven Threat Intelligence
Cyber-Insurance: Safety Net or False Security?
Creating a Culture of Security Awareness Training
Recovery Playbook: From Immutable Backups to Incident Response
Futureproofing: What’s Next for Ransomware Defenses
1. The Escalating Ransomware Landscape in 2025
Ransomware attacks surged 67 % year-over-year, costing global businesses an estimated $30 billion in direct payouts, downtime, and reputational damage. Criminal syndicates now deploy double-extortion, threatening to leak data even after payment. As an IT leader, recognizing ransomware as not if, but when is the first step toward resilience.
Highlight for internal link: “latest cybersecurity statistics”
2. Why Small- and Mid-Sized Businesses Are Prime Targets
Contrary to popular belief, enterprise giants aren’t the only bull seyes. SMBs typically run lean IT teams and postpone critical patches—making them low-hanging fruit. Attackers exploit remote-desktop protocols and unprotected SaaS integrations to infiltrate networks within minutes.
Highlight for internal link: “best patch-management tools”
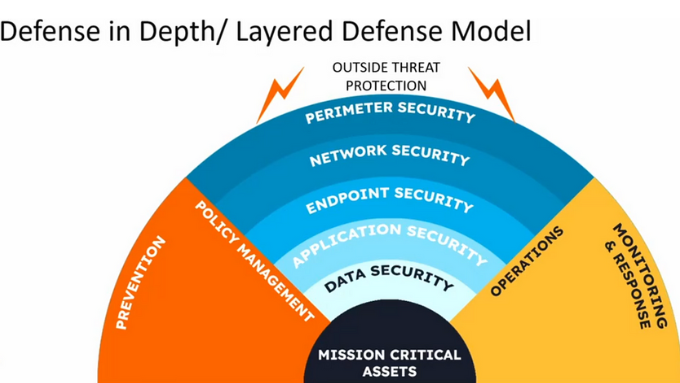
3. Ransomware Protection Strategies: A 360° Blueprint
A layered defense beats point solutions. Combine robust ransomware protection strategies with proactive monitoring, airtight policies, and well-rehearsed incident-response drills. View security as a continuous lifecycle: Predict → Prevent → Detect → Respond → Recover.

4. Building a Zero-Trust Security Framework
The perimeter is dead; identity is the new firewall. A zero-trust security framework requires continuous verification of users, devices, and workloads.
Micro-segmentation: Isolate critical workloads.
Least-privilege access: Enforce role-based permissions.
Adaptive MFA: Dynamically adjust authentication based on risk signals.
Highlight for internal link: “zero-trust architecture checklist”
5. The Role of Endpoint Detection and Response (EDR)
Modern EDR solutions use behavioral analytics to flag suspicious encryption activity in real time. Choose a platform that offers:
Real-time rollback to a pre-infection snapshot.
Cloud-native threat hunting with MITRE ATT&CK mapping.
Automated containment—quarantining affected hosts within seconds.
Highlight for internal link: “top EDR platforms compared”
6. Leveraging AI-Driven Threat Intelligence
Attackers innovate; defenders must out-innovate. AI-driven threat intelligence ingests billions of signals—dark-web chatter, IOC feeds, anomaly logs—to predict ransomware campaigns before they hit your perimeter. Integrate this data into your SIEM for enriched alerts and faster triage.
Highlight for internal link: “how threat intelligence feeds work”
7. Cyber-Insurance: Safety Net or False Security?
Policies can offset financial loss, but insurers increasingly mandate security controls—MFA, patched VPNs, immutable backups—before underwriting coverage. Treat cyber-insurance as a supplement, not a substitute, for comprehensive security posture.
Highlight for internal link: “cyber-insurance requirements 2025”
8. Creating a Culture of Security Awareness Training
Human error triggers 88 % of breaches. Quarterly security awareness training transforms employees from liabilities into sentries:
Phishing simulations boost detection rates.
Just-in-time coaching embeds micro-lessons during risky clicks.
Gamification keeps engagement high and retention longer.
Highlight for internal link: “designing engaging security games”
9. Recovery Playbook: From Immutable Backups to Incident Response
Even fortress-grade defenses can crack. A timed, tested recovery plan minimizes business impact.
Immutable, air-gapped backups—offline or WORM-storage.
Runbook automation—orchestrate isolation, forensic imaging, and legal notification steps.
Tabletop exercises—stress-test your plan against worst-case scenarios.
Post-mortem review—feed lessons learned back into controls.
Highlight for internal link: “building an incident-response runbook”
10. Futureproofing: What’s Next for Ransomware Defenses
Quantum-resistant encryption, hardware-rooted security, and fully homomorphic data processing are emerging frontiers. Meanwhile, regulatory frameworks—like the EU’s NIS2 and the U.S. SEC’s cyber-disclosure rules—tighten breach-reporting timelines. Staying compliant is no longer optional; it’s branding.
Highlight for internal link: “upcoming cybersecurity regulations”
| Priority | Action Item | Owner | Deadline |
|---|---|---|---|
| 🔒 High | Deploy EDR with automated rollback | SecOps | 30 days |
| 📑 High | Implement zero-trust segmentation | NetOps | 60 days |
| 🗄️ Medium | Configure immutable, off-site backups | IT Ops | 45 days |
| 🧠 Medium | Launch quarterly phishing simulation | HR & IT | 14 days |
| 🛡️ Low | Evaluate cyber-insurance renewal | CFO | 90 days |
Final Thoughts
Ransomware is the defining cyber-threat of 2025. By integrating ransomware protection strategies—from a zero-trust security framework and robust endpoint detection and response to AI-driven threat intelligence and continuous security awareness training—your business can pivot from reactive firefighting to proactive resilience. Act now, iterate often, and you’ll transform ransomware from existential crisis into manageable risk.
Ready to dive deeper? Check our guides on the latest cybersecurity statistics, zero-trust architecture checklist, and top EDR platforms compared to strengthen your security posture today.
